Simple,
secure,
and swift.
Choose all three.
secure,
and swift.
Choose all three.
Jonathan Michael
VO
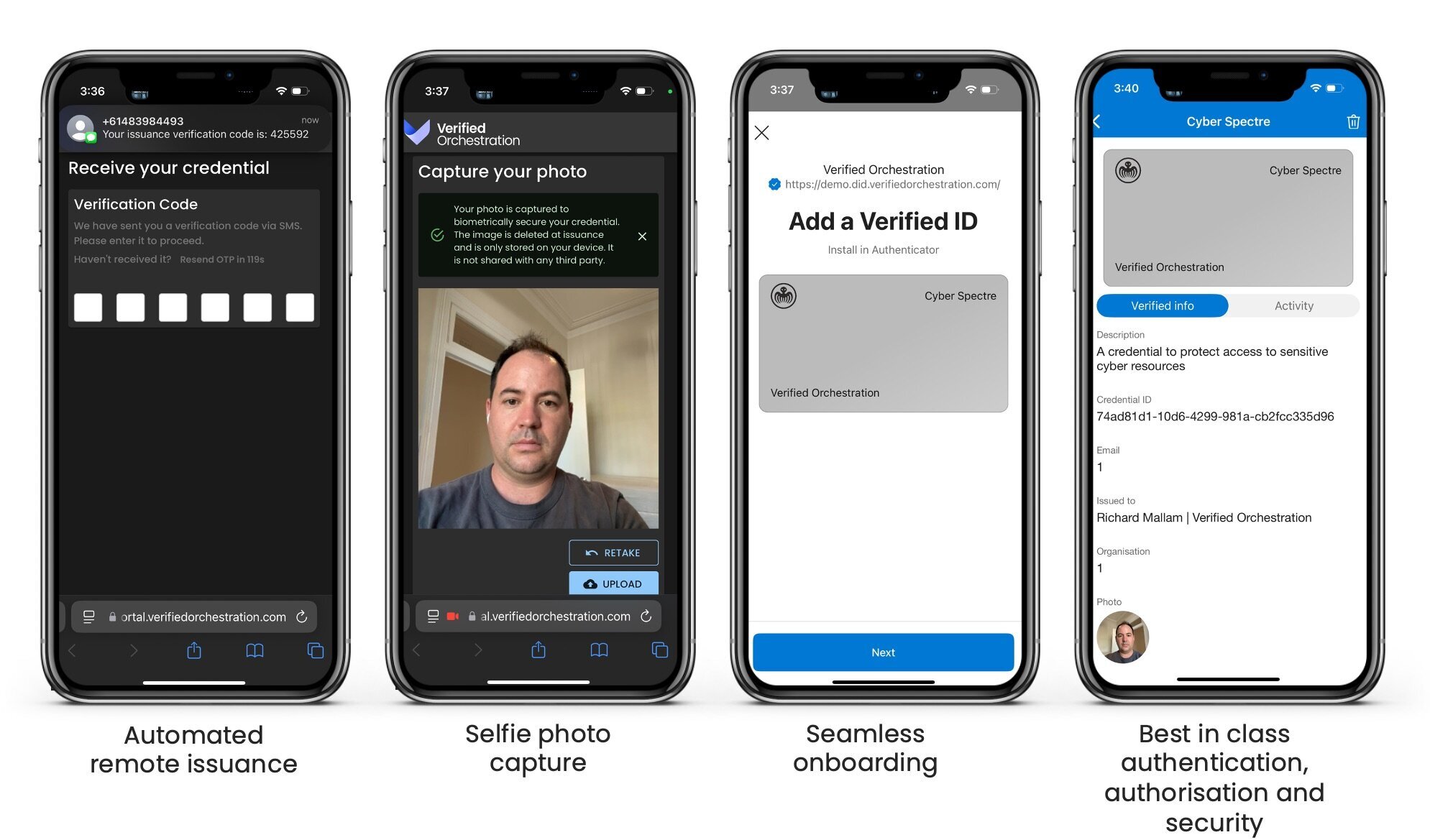
Not another Identity Provider
- Integrate with your existing Identity Provider using open standards
- No end user data stored in the VO solution
- Immutable transaction signing
- Enable bi-directional verification flows
- VCs are stored in the end user's wallet
- Phishing-resistant
- Cryptographically secure
- Configure authentication and authorisation flows to suit specific Levels of Assurance
"At least 500 million smartphone users will be using a Digital Identity Wallet by 2026"
Akif Khan, VP Analyst at Gartner
Gartner Security & Risk Management Summit, London, September 2024
Rapid time to value
Verifiable Credentials made easy for organisations of all sizes.
Leverage our secure platform to uplift your Digital Identity capability. Integrate with your existing Identity Provider using open standards, without migrating user data.
- Turnkey SaaS solution
- Integrate using APIs and open standards
- Low ongoing costs
Benefits realised post-implementation
Secure your organisation
Secure your organisation
Plain text usernames and passwords are vulnerable, and a poor user experience, even with SMS OTPs
- SMS OTPs and other MFA mechanisms introduce friction for end users, are expensive to maintain, and have their security worries
- Secret questions, like mother's maiden name, are no longer secret, thanks to data breaches
The VO platform enables phish-resistant and tamper evident credentials that secure your organisation and users - Verifiable Credentials reduce your cybersecurity risk and modernise your security posture
53%
of consumer self-reported cyber crime could be mitigated by more secure authentication methods.
ASD cyber threat report 2023–24
Improve user experience
42%
of shoppers will abandon their purchase if the process is complex or intrusive
Baymard Research 2022
Improve user experience
- On-board end users rapidly and securely
- Authenticate users using flexible authentication flows, with Levels of Assurance tailored to the transaction
- Authorise access and transactions seamlessly, improving process completion, reducing delays, increasing revenue
Reduce Cost
Reduce Cost
Defeat fraudsters by replacing traditional paper- or screenshot-based on-boarding
- Link Verifiable Credentials to existing IDV processes, reducing the need for ongoing identity verification
- Integrate with existing Identity and Access Management services, without migrating end user credentials or data
- Reduce the cost of cybersecurity with modern Verifiable Credentials, from VO
20%
of fraud in the UK is a result of Identity Theft
Alloy UK State of Financial Crime Benchmark Report, 2024
More than just authentication
Enable straight-through processing
Enable straight-through processing
24%
of applications with inconsistent PII, an indication of synthetic fraud
Alloy State of Fraud Benchmark Report, 2024
Enable straight-through processing with trusted, immutable data
More secure authentication is just the start.
Enable straight-through-processing, with authorisation based on data managed in the user's credentials.